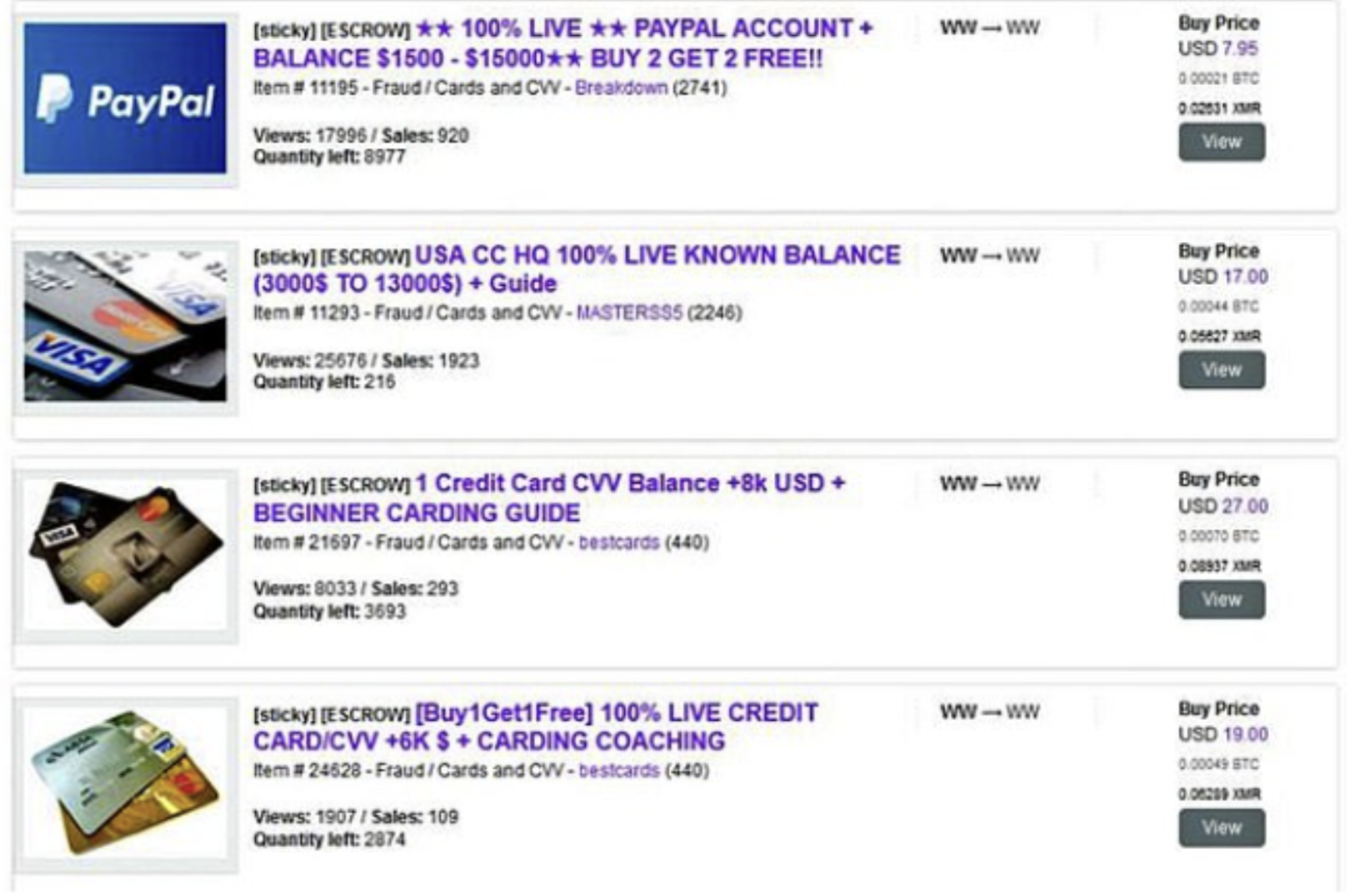
The Dark Web works by deploying specialized tools and protocols that enable users access to intended websites to conduct transactional activities anonymously. The Dark Web is a subset of the Deep Web that is intentionally hidden and requires special browser, such as Tor, to access Dark Web resources. It is often used for nefarious activities (56.8%), such as buying and selling of stolen digital data. The Dark web is not indexed by search engines; however, your IT Managed Services provider can help you locate these sites if there is a requirement.
The Tor Network
The Tor (The Onion Router) network is a critical part of the dark web. It allows users to browse anonymously by routing their internet traffic through a series of volunteer-operated servers (nodes). Each node only knows the previous and next node in the chain, ensuring privacy. The final exit node connects to the regular internet, allowing users to access hidden services.
Onion Routing
Tor uses onion routing, where data packets are encrypted in layers (like an onion) as they pass through nodes. Each node peels off one layer, revealing the next destination. This process ensures anonymity and prevents anyone from tracing the entire route.
Hidden Services
Websites on the dark web are called hidden services. They use “.onion” domain names and can only be accessed through the Tor network. These sites don’t appear in conventional search engines and are often associated with illegal activities.
Anonymity and Encryption
Tor provides anonymity by masking users’ IP addresses. It also encrypts data between nodes, making it difficult for anyone (including law enforcement) to intercept communications. However, this encryption can be used for both good (whistleblowing, privacy) and evil (illegal activities).
Anonymity and Encryption
Tor provides anonymity by masking users’ IP addresses. It also encrypts data between nodes, making it difficult for anyone (including law enforcement) to intercept communications. However, this encryption can be used for both good (whistleblowing, privacy) and evil (illegal activities).
Remember that while the dark web has a reputation for illicit activities, it also serves as a platform for privacy-conscious individuals and activists. It’s a complex ecosystem with both positive and negative aspects.
If you have concerns about employees possibly knowing how the Dark Web works and accessing the Dark Web on company resources, contact ION Technology Group today for a detailed review at 1.856.719.1818 or at service@iontg.com.






